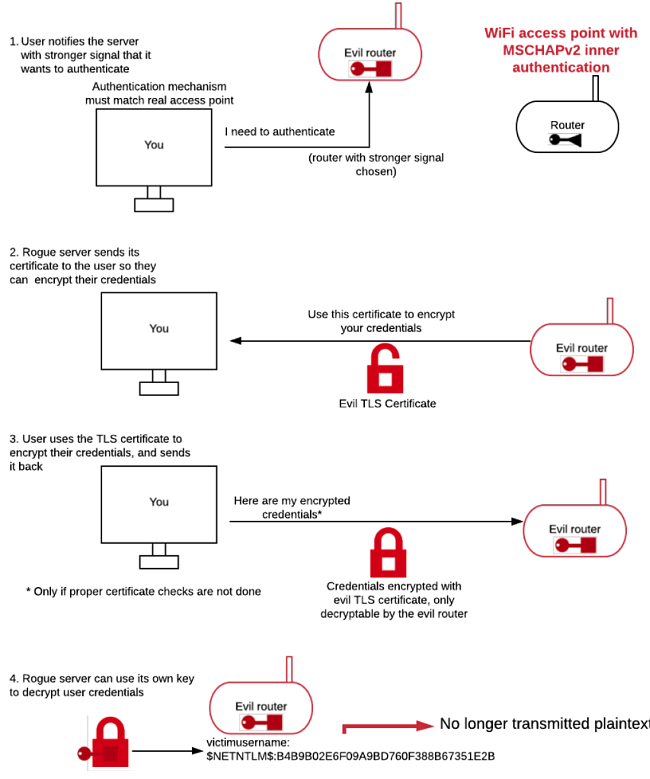
Universities' Security Blindspot on Global Free WiFi Network Leaves Faculty and Student Usernames and Passwords Exposed to Hackers

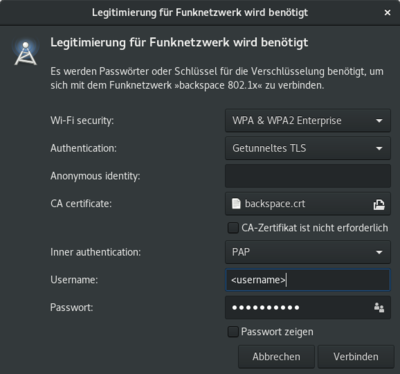
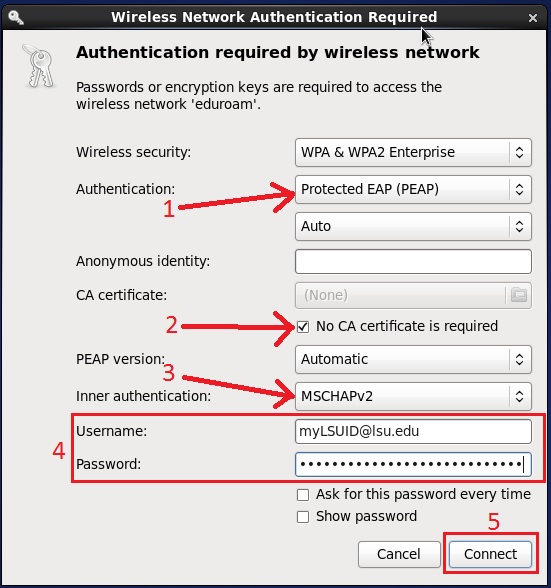
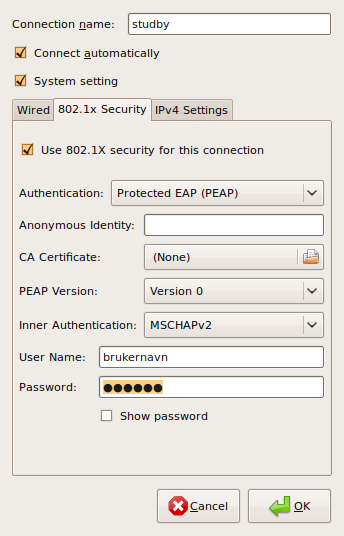
networking - How to connect to PEAP enterprise wifi networks that has no inner authentication - Ask Ubuntu

Understanding Authentication Policies > Authentication and Authorization Policies: Using Cisco Identity Services Engine in a BYOD World | Cisco Press
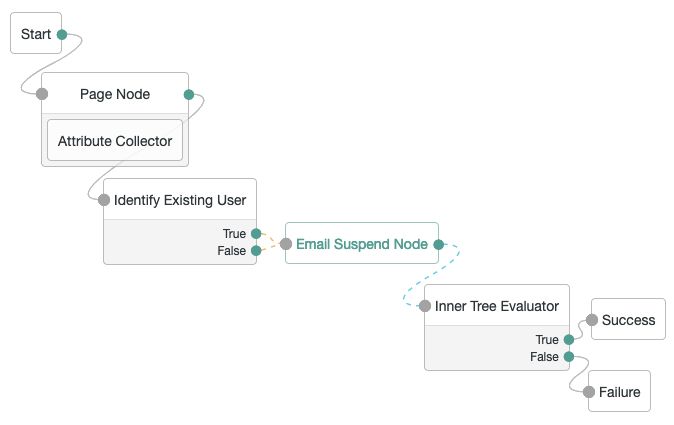
ForgeRock Access Management 7.1.4 > Authentication and Single Sign-On Guide > Suspended Authentication
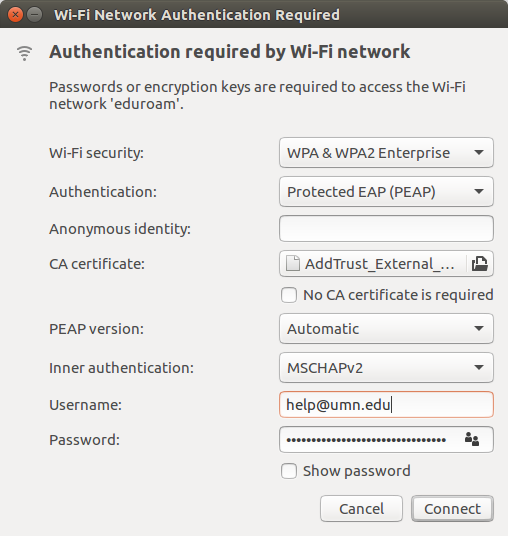
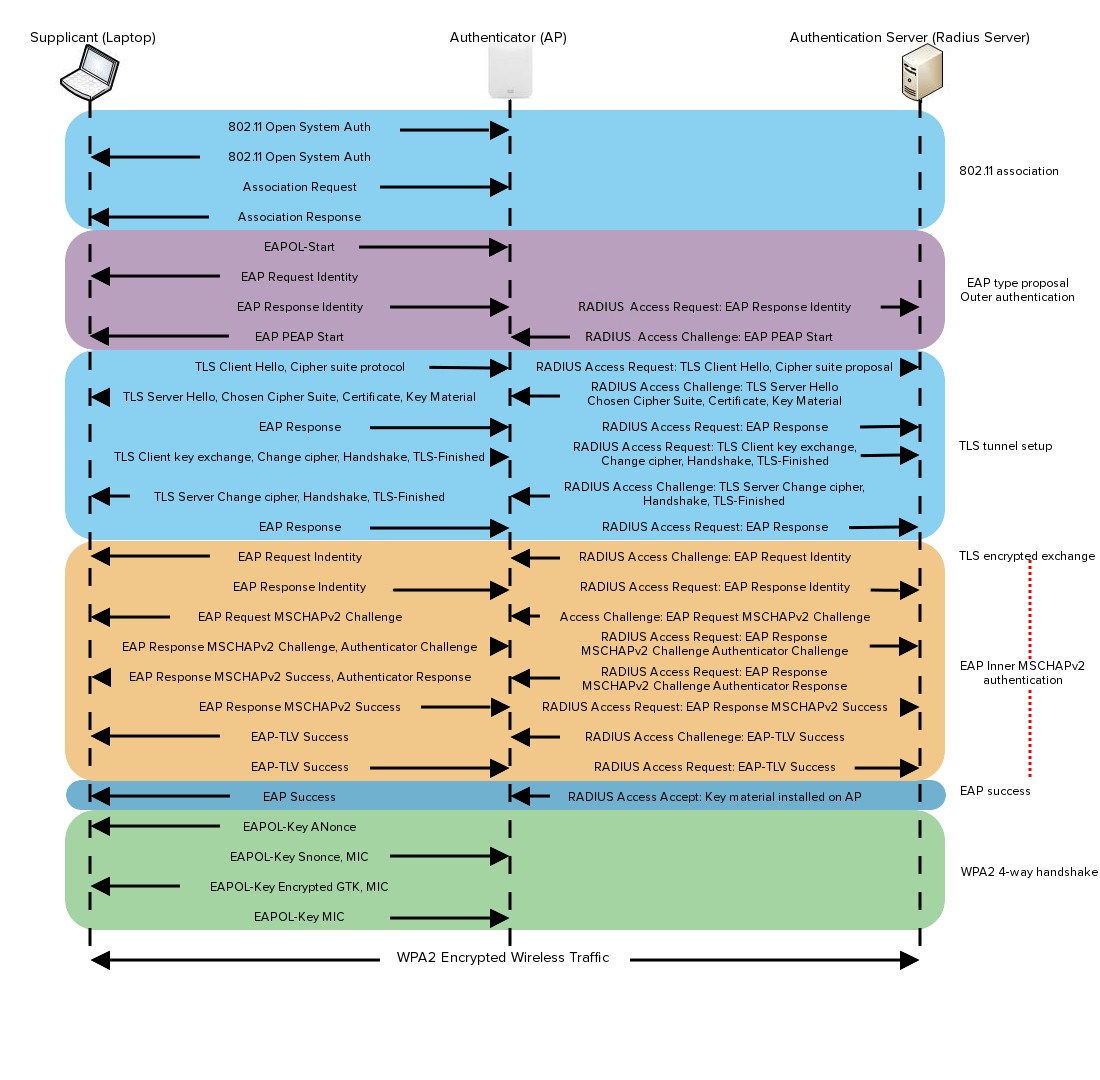

![services:wifi:lin:ubuntu [SISSA ITCS] services:wifi:lin:ubuntu [SISSA ITCS]](https://www.itcs.sissa.it/_media/services/wifi/lin/wifi_ub2.jpeg)



![MS-PEAP]: Overview | Microsoft Learn MS-PEAP]: Overview | Microsoft Learn](https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-peap/ms-peap_files/image001.png)
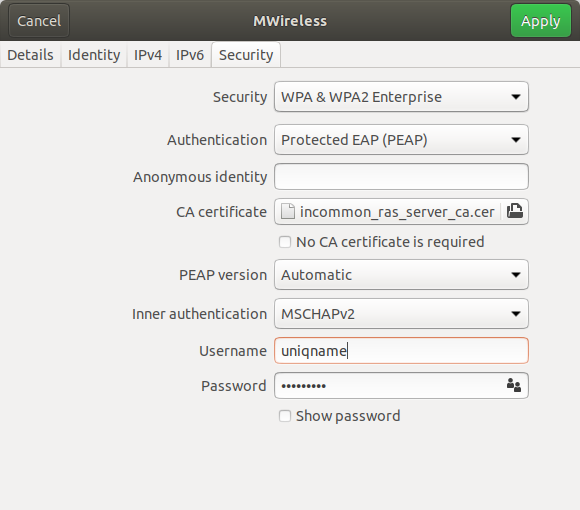
![connect:wifi-linux [Area dei Servizi ICT - Documentation] connect:wifi-linux [Area dei Servizi ICT - Documentation]](https://docu.units.it/dokuwiki/_media/connect:linux:ubu10.20.png)