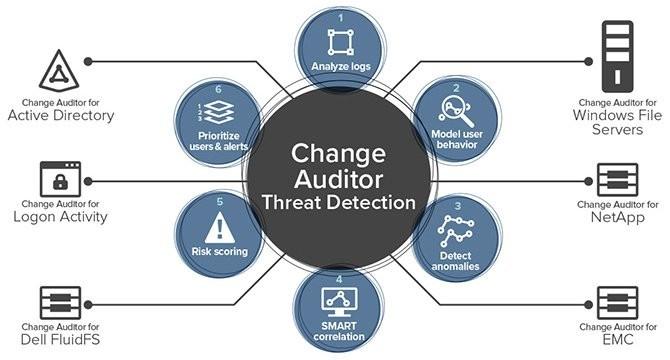
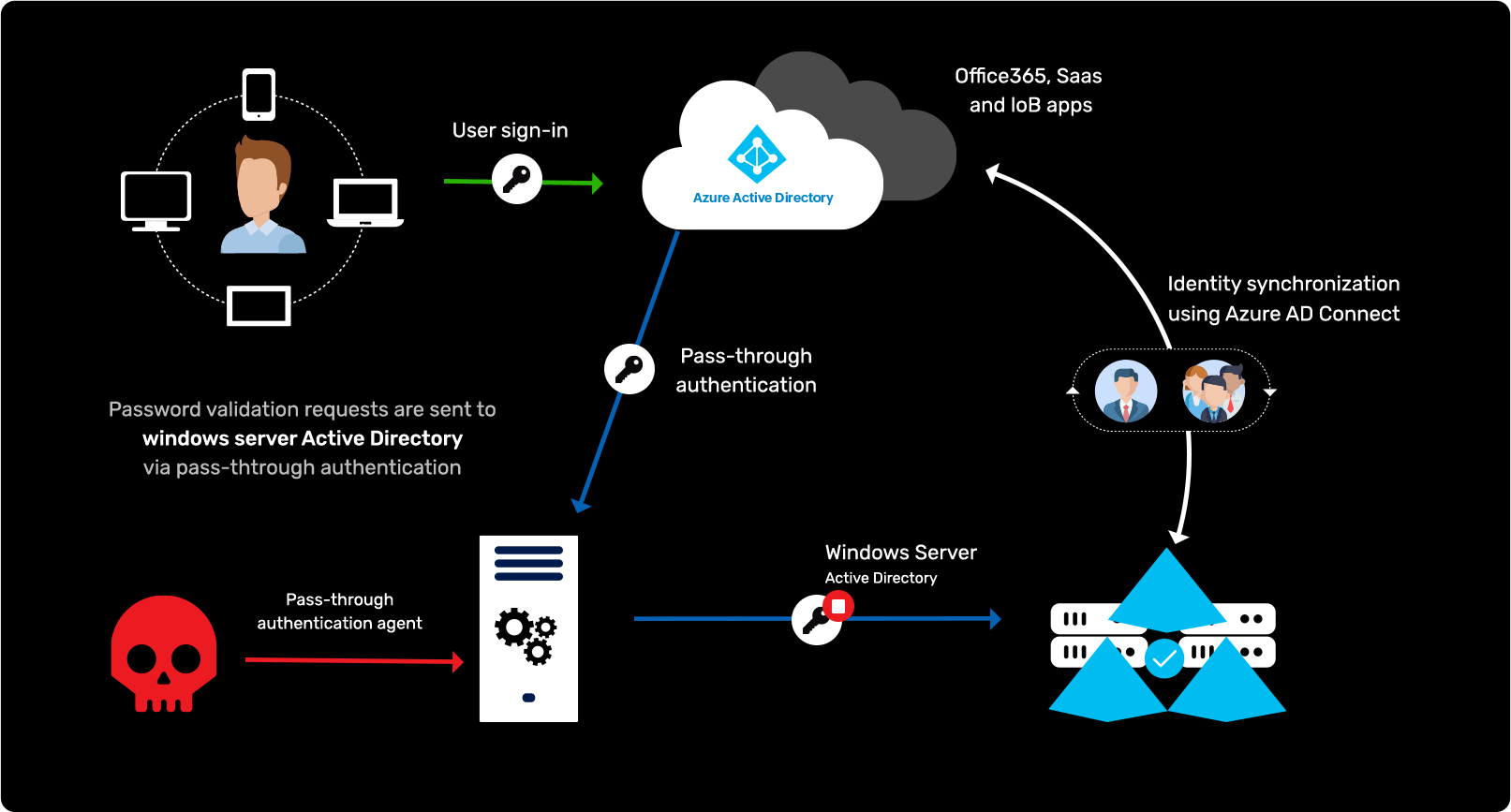
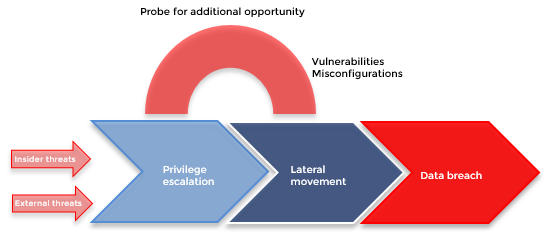
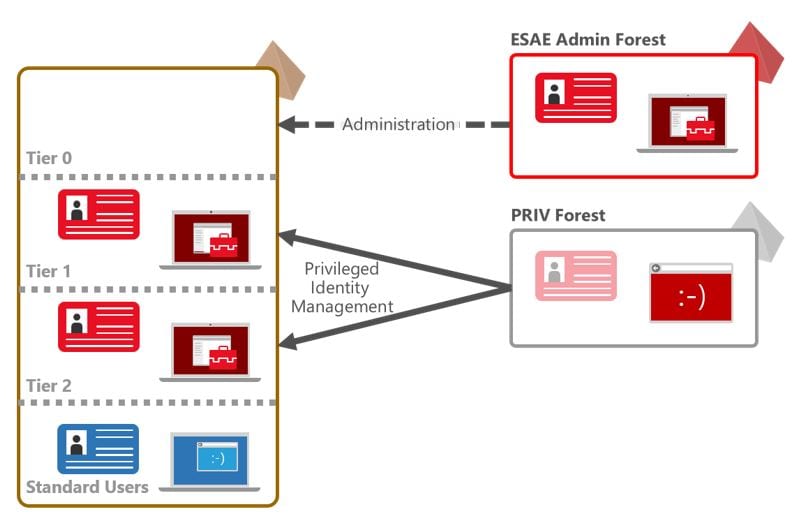
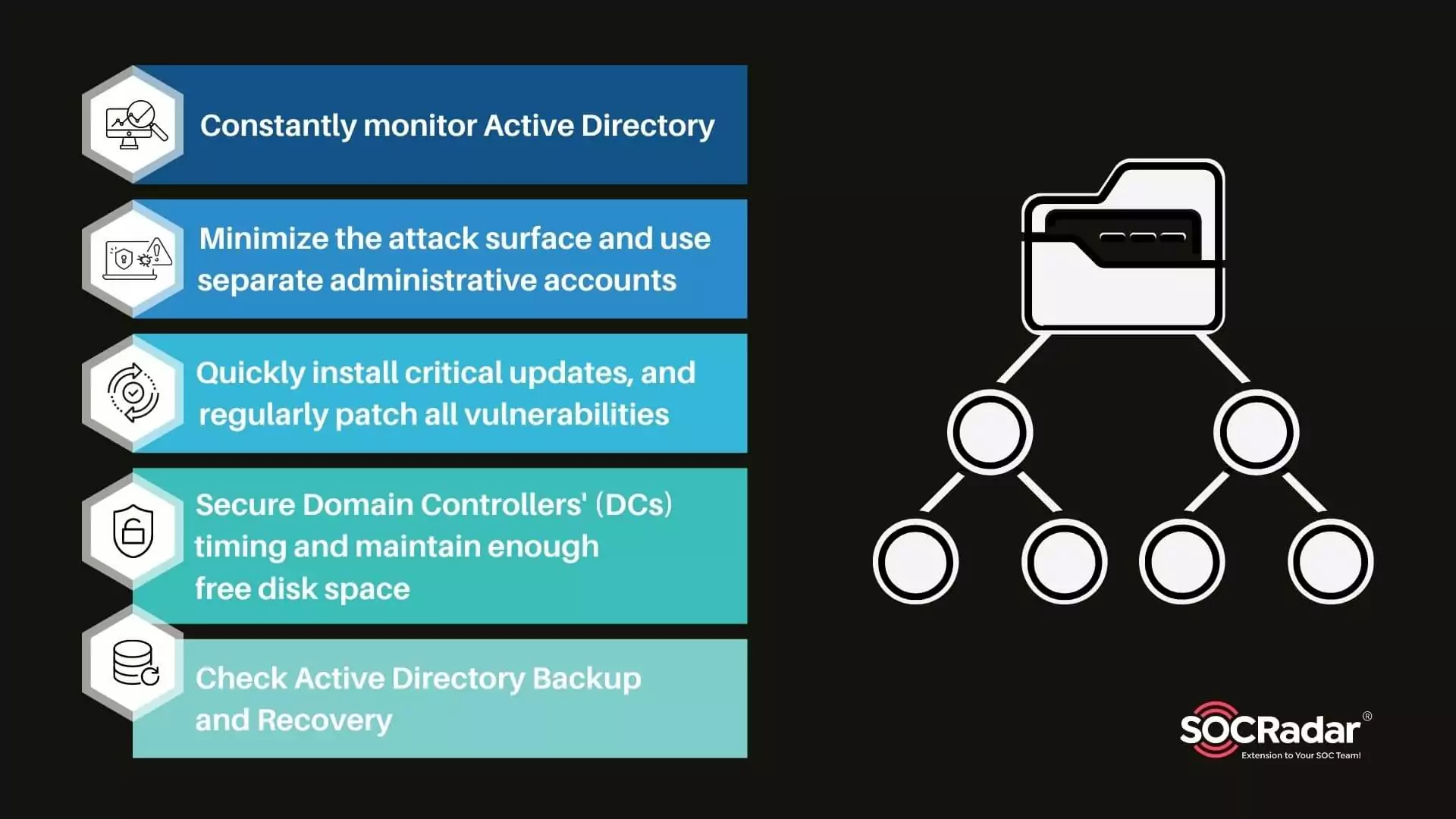
Pentester Academy on Twitter: "Understand and practice the basics of attacking Active Directory using metasploit and other tools in our Attacking Active Directory with Linux lab. #LinuxAD https://t.co/nEuJFib30U https://t.co/PRGQlnsuqU" / X

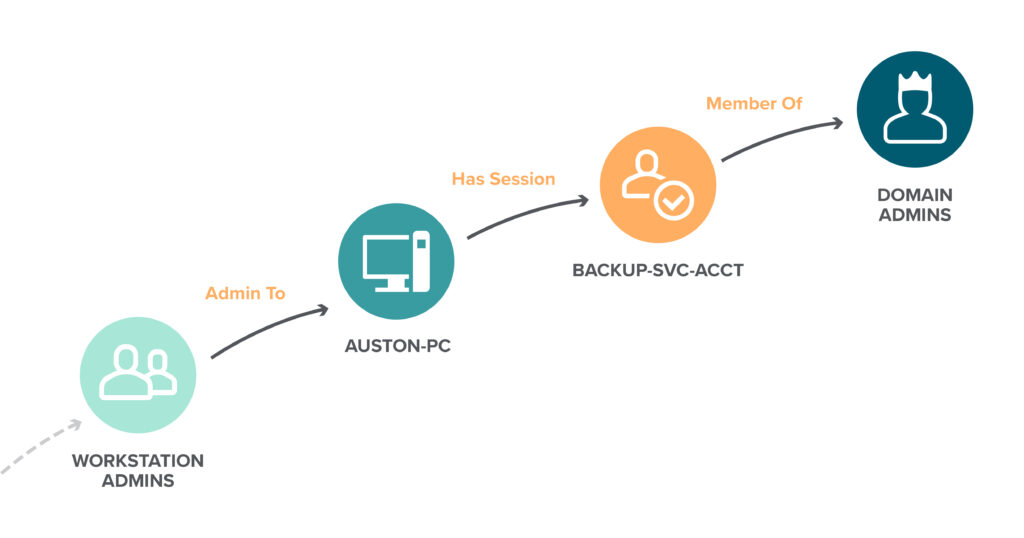
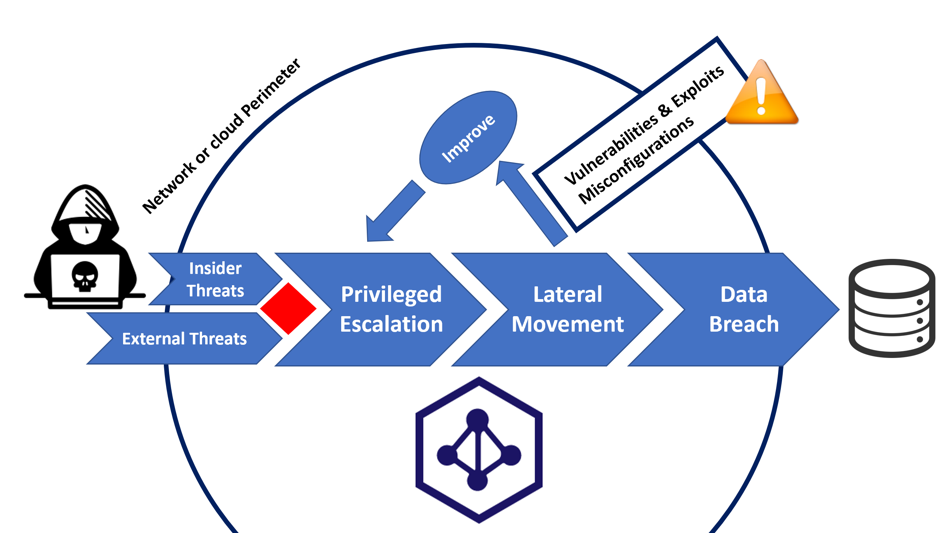
Why Active Directory Attack Paths are the Secret to Many Successful Ransomware Attacks - My TechDecisions